Audit log
The audit log keeps track of all the user actions and is a great way to see what was done by who and when. In addition to this data, it includes the network IP, the user agent and geographical location from where the action was originated.
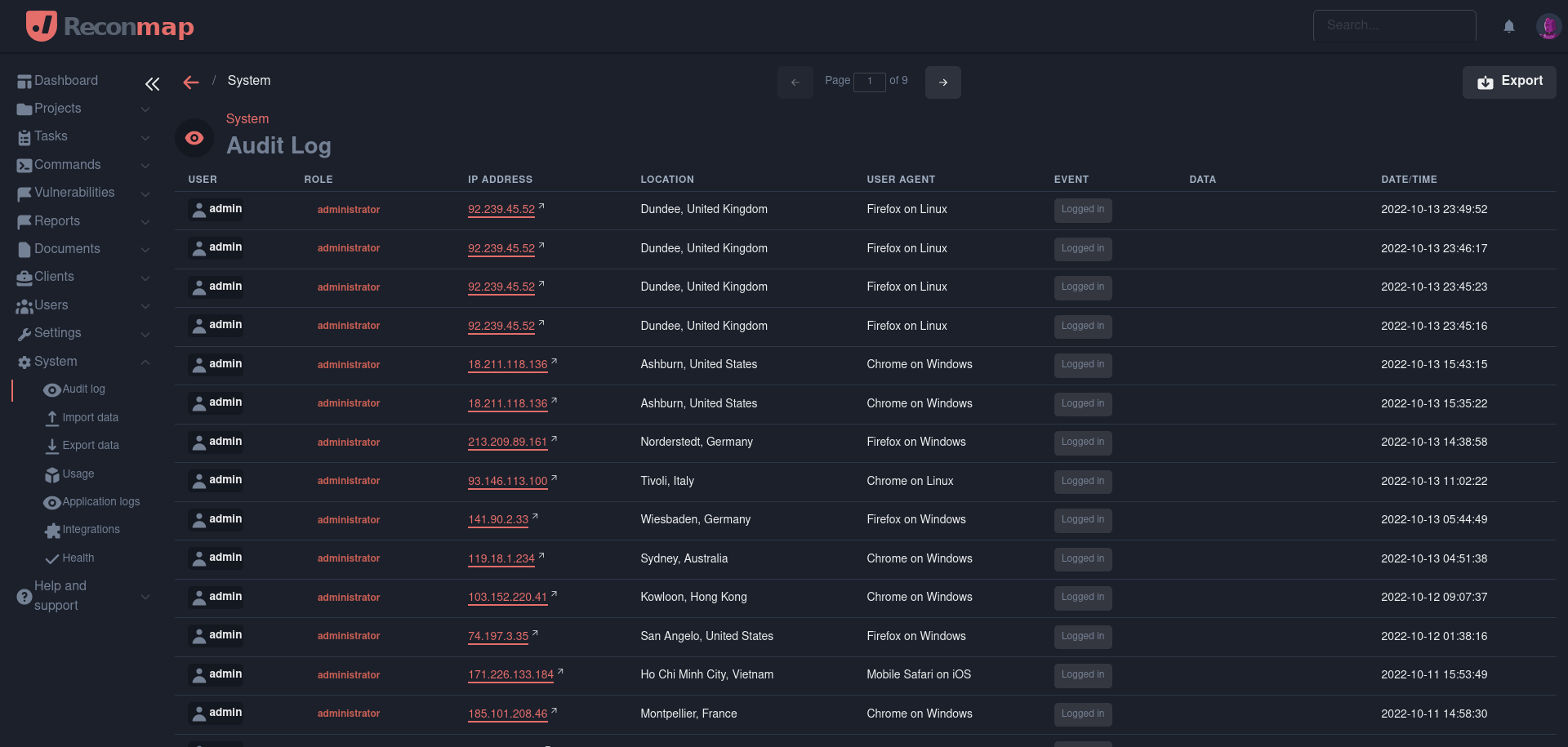
Al the data in the audit log is permanent and non-modifiable.
The audit log keeps tracks of all following actions and many others:
- User logged in
- User logged out
- User created
- User modified
- User deleted
- Integration enabled
- Integration disabled
The audit log information can be exported to CSV to do aggregation and analysis.