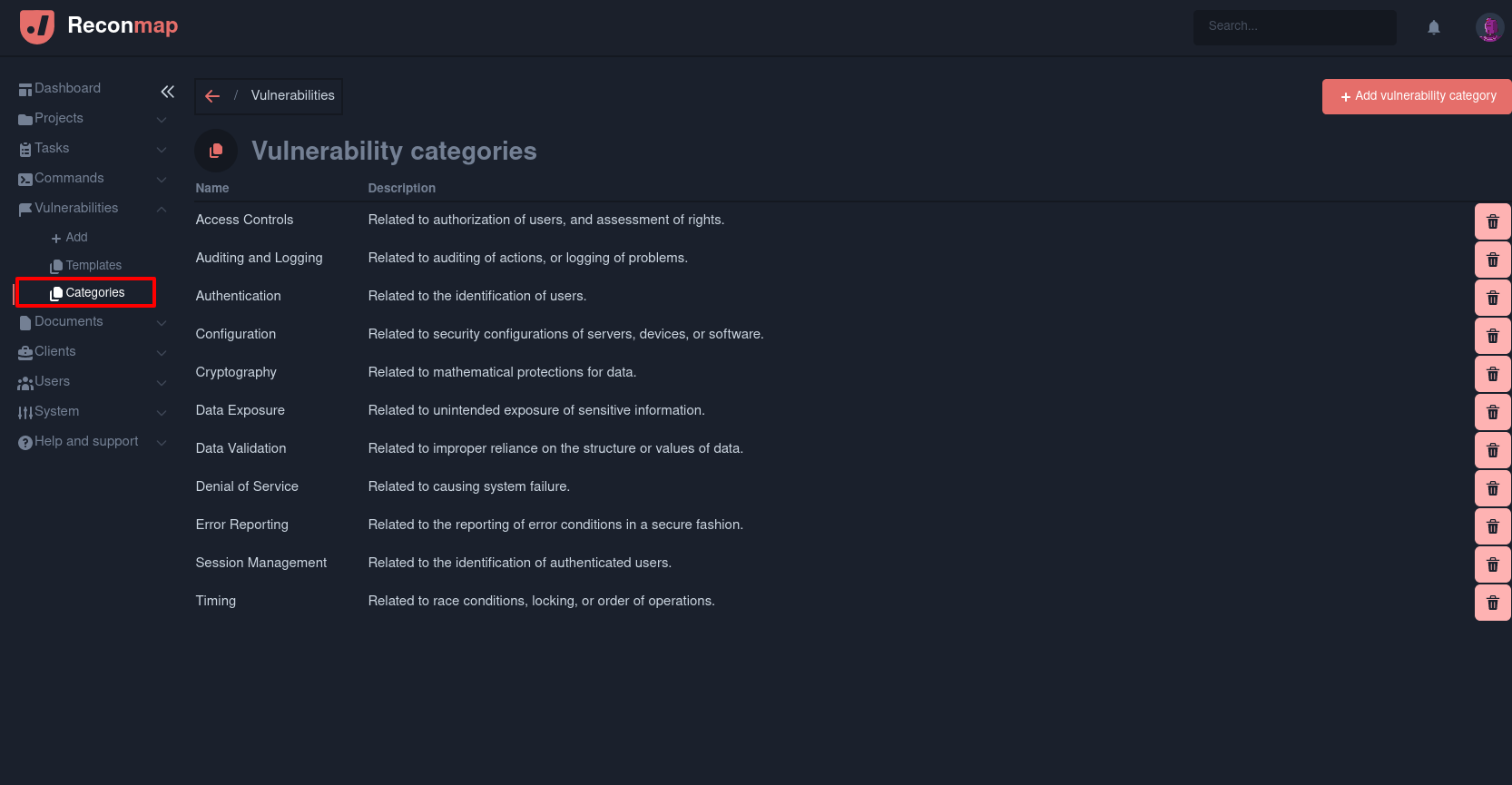
Vulnerability categories
In Reconmap all vulnerabilities are associated to one category. The default categories are
- Access Controls: Related to authorization of users, and assessment of rights.
- Auditing and Logging: Related to auditing of actions, or logging of problems.
- Authentication: Related to the identification of users.
- Configuration: Related to security configurations of servers, devices, or software.
- Cryptography: Related to mathematical protections for data.
- Data Exposure: Related to unintended exposure of sensitive information.
- Data Validation: Related to improper reliance on the structure or values of data.
- Denial of Service: Related to causing system failure.
- Error Reporting: Related to the reporting of error conditions in a secure fashion.
- Patching: Related to keeping software up to date.
- Session ManagementRelated to the identification of authenticated users.
- Timing: Related to race conditions, locking, or order of operations.
Custom categories
The user can add or remove any number of additional categories to the system using the Vulnerability categories page.